In a world where the digital landscape is increasingly becoming hostile, nonprofit open-source foundations dedicated to improving security, such as the OWASP, serve a critical role.
OWASP is an online community that offers open-source educational resources to developers, designers, architects and business owners about the risks associated with the most common web application security vulnerabilities.
In this blog, we’ll talk more about what is OWASP and what are the OWASP top 10 cybersecurity vulnerabilities.
What is OWASP?
Open Web Application Security Project (OWASP) is an international non-profit organization dedicated to web application security. Everybody can improve their own web application security by using OWASP’s materials, which are free and easily accessible on the website. OWASP offers documentation, tools, videos, articles and forums to help businesses and individuals learn about the prominent web application security vulnerabilities.
What is the OWASP Top 10?
One of the most popular projects of the OWASP foundation is the OWASP Top 10, which identifies the ten most prominent threats to today’s applications. It’s meant to get executives and developers thinking about the most critical security risks.
The goal of the OWASP’s Top 10 is not to enumerate ten explicit threats. It’s to prompt software development teams to shift their cultures to write more secure code. The list of OWASP top ten security vulnerabilities explains the most prominent web application security vulnerabilities and provides potential mitigation strategies for preventing them.
You might be interested in: Top 10 most effective procedures for mobile app protection
List of OWASP Top 10 Security Vulnerabilities
Last updated in 2021, the top 10 security risks OWASP identified are listed as the following:
1- Injection
Injection attacks involve malicious input from external sources, such as databases or the internet, that are used to manipulate application data. This type of attack is most common with web-based applications and can lead to remote code execution and data theft. Examples of injection attacks include SQL injection, LDAP injection, and script injection.
2- Broken Authentication and Session Management
Broken authentication and session management involves the mishandling of user credentials or the sharing of user session information with unauthorised parties. Examples include passwords stored in plaintext, cross-site scripting (XSS) flaws, and session hijacking.
3- Cross-Site Scripting (XSS)
Cross-site scripting (XSS) is a type of injection attack that involves injecting malicious scripts into web pages in order to execute code in the browser. XSS can lead to session hijacking, data theft, and other malicious activities.
4- Broken Access Control
Broken access control refers to the lack of proper authentication checks for users accessing restricted resources. Examples include missing authorization controls, bypassing access control mechanisms, and allowing users to gain access to system files or databases without the necessary permissions.
5- Security Misconfiguration
Security misconfiguration occurs when an application is improperly configured and opens up security vulnerabilities. Examples include weak passwords, incorrect file permissions, disabled security settings, and vulnerable system components.
6- Insufficient Authorization and Authentication
Insufficient authorization and authentication refer to situations where an application does not properly check user credentials before allowing access to restricted resources. Examples include failing to use secure authentication protocols or relying on default settings.
7- Insecure Cryptographic Storage
Insecure cryptographic storage involves the improper storage of sensitive data in an insecure format. Examples include storing passwords in plaintext, using weak encryption algorithms, and leaving keys exposed.
8- Tampering with Data
Tampering with data involves altering information stored in the application without authorization. Examples include changing fields in a database or manipulating data sent over the network.
9- Using Components With Known Vulnerabilities
An application’s use of a library or framework with a known vulnerability can grant a successful attacker access to the same internal resources that the application itself has, depending on what privileges the application has.
A possible result could be anything from the deletion of personal data to the ability to run malicious code remotely. Malicious adversaries can also leverage common vulnerabilities present in web applications as an entry point to gain unauthorised access to critical assets.
10- Insufficient Logging & Monitoring
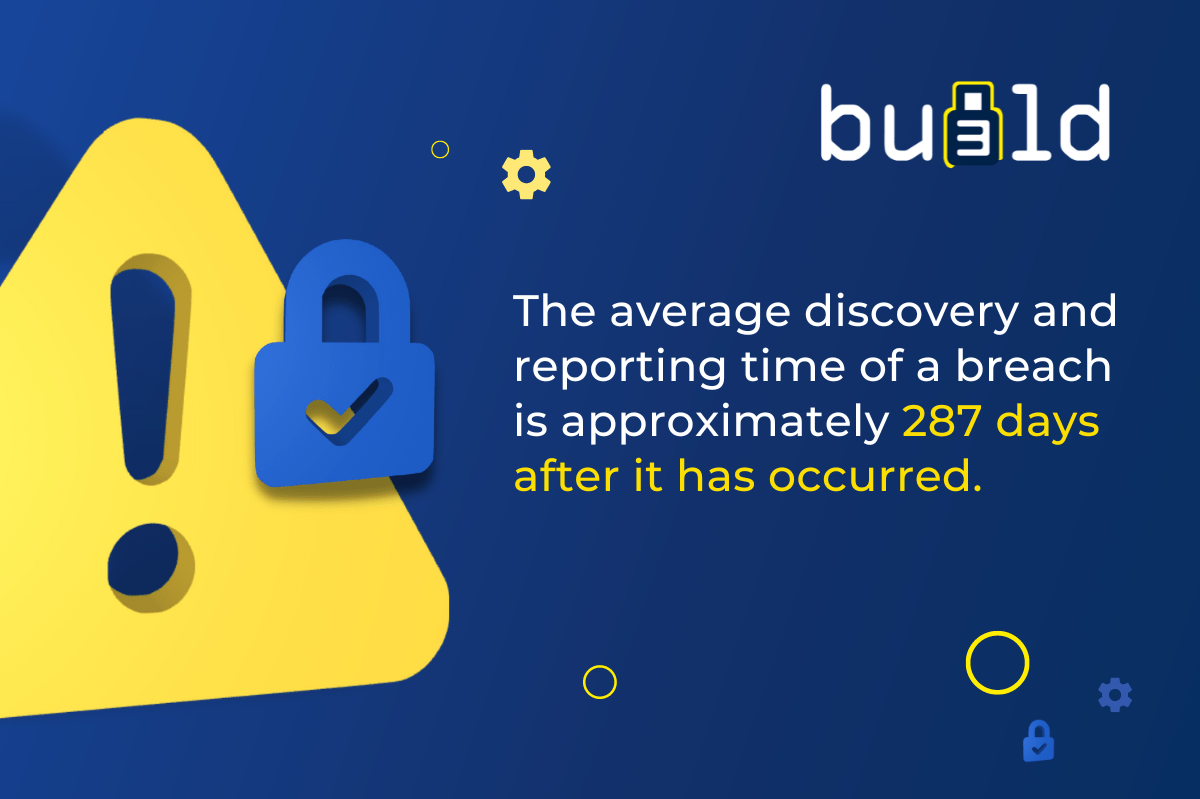
Many web applications lack the ability to timely detect a malicious attempt or a security breach. In fact, according to experts, the average discovery and reporting time of a breach is approximately 287 days after it has occurred. This enables attackers to do a lot of damage before there is a response.

The OWASP advises that developers of web applications implement logging, monitoring, and a response plan in order to notice and thwart attack attempts.
Build38 can help you protect your apps
The OWASP Top 10 is a great resource for organizations and security professionals to understand the current and emerging threats that they need to be aware of. It’s essential for businesses to have a comprehensive understanding of these common security vulnerabilities in order to properly protect their systems and data.
By being familiar with the OWASP Top 10 and following the best practices outlined in the OWASP Top 10, organizations can better secure their environment and ensure that their systems remain secure and protected against potential threats.

Hi, this is a comment.
To get started with moderating, editing, and deleting comments, please visit the Comments screen in the dashboard.
Commenter avatars come from Gravatar.